Bybit Hack Case: The Largest Cryptocurrency Heist Revealed
**In its newly released Cyber Threat Situation Report, STM has shed light on the biggest cryptocurrency theft in history, known as the “Bybit Hack Case.”** This meticulously prepared report, crafted by STM’s cybersecurity specialists, covers notable incidents and trends in cybersecurity for the first quarter of 2025. Among the various topics addressed, the Bybit hack stands out, illustrating the serious vulnerabilities within cryptocurrency exchanges amidst growing digital warfare.
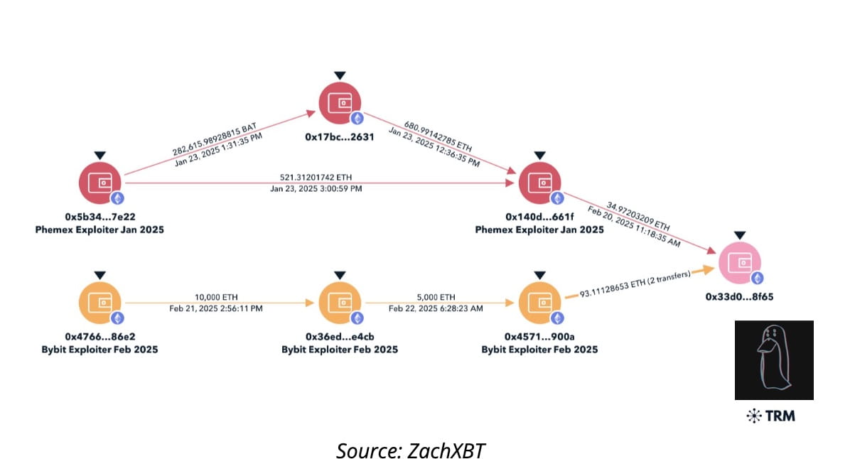
In February 2025, the cryptocurrency landscape experienced a significant upheaval following a cyberattack on Bybit, a leading cryptocurrency exchange headquartered in Dubai. This breach, which marked the largest theft in cryptocurrency history, resulted in the loss of approximately 400,000 Ethereum tokens, valued at around $1.5 billion. The incident came to light on February 21 when Bybit identified a vulnerability exploited during a routine transfer from a cold wallet to a hot wallet. Malicious actors manipulated this process to redirect sizable funds into their own accounts.
The Role of Lazarus Group in the Heist
Investigations into the breach revealed that the notorious North Korean-backed hacker group, Lazarus, was behind the attack. The FBI’s inquiry into the incident confirmed that the stolen Ethereum tokens were swiftly converted into Bitcoin and other digital currencies, effectively obscuring their origin. These assets were then dispersed across thousands of different blockchain addresses to hinder tracing efforts. Lazarus is infamous for its involvement in several high-profile cyberattacks, including the disruption of Sony Pictures and attacks on banking systems globally.
According to TRM Labs, a leading firm in blockchain intelligence, North Korean hackers have been implicated in stealing over $5 billion worth of cryptocurrencies since the onset of 2017. This alarming statistic underscores the urgency for cryptocurrency exchanges and users alike to fortify their security measures against such sophisticated cyber threats. The STM report underscores the necessity of implementing multi-signature wallets and conducting regular security audits to mitigate risks.
Addressing Human Factors in Cybersecurity
The report also highlights the significant impact of human factors in cybersecurity breaches. Often seen as the weakest link in the security chain, human error plays a crucial role in facilitating these attacks. The STM study points to the need for robust measures, including the use of strong, unique passwords changed regularly and the activation of multi-factor authentication (MFA). It emphasizes the need for regular training for employees to recognize and avoid phishing attempts.
Furthermore, the report advises against the uncontrolled use of USB drives and other portable media, which can serve as gateways for malware infections. Employees should also undergo simulated attack tests to build resilience against potential cybersecurity breaches. By addressing these human vulnerabilities, organizations can significantly reduce the likelihood of successful cyberattacks.
Geographic Insights into Cyberattacks
Moreover, the STM report provides insights into the geographical distribution of cyberattacks, revealing that the United States and the Netherlands were responsible for the highest number of incidents recorded between January and March 2025. The US accounted for 26% of all attacks, while the Netherlands followed closely with 15%. Other countries contributing to the growing list include India, China, Taiwan, France, Japan, the UK, the UAE, and Kenya.
This data underlines the international nature of cyber threats and the necessity for global collaboration in enhancing cybersecurity measures. As cybercriminals often operate across borders, a concerted effort among nations can assist in counteracting these nefarious activities more effectively.
Conclusion and Future Recommendations
In conclusion, the STM’s Cyber Threat Situation Report emphasizes the urgent need for cryptocurrency exchanges to adapt and evolve in response to these rising threats. The Bybit hack case serves as a stark reminder of the vulnerabilities inherent in the cryptocurrency ecosystem. To safeguard against potential future breaches, it is critical for exchanges to develop improved protocols for cold wallet usage and reinforce their security frameworks.
As the battle against cyber threats escalates, organizations must invest not only in technology but also in the human elements that underpin cybersecurity. Continuous training, awareness campaigns, and collaboration across borders will be vital in mounting a robust defense against cyberattacks and ensuring the safety of digital assets.